Anatomy of a good Social Engineering/Phishing attack!
Social Engineering and Phishing has been around for donkeys’ years now. While really sophisticated attacks are usually designed and prepped months, sometimes years in advance, and can be brutally effective, small scale attacks are what brings in the moolah!
This is because while bigger attacks are usually constrained by time, money and the sheer specificity of the attack vector you are targeting, a smaller, easily replicated, but en massé attack, can often bring in more returns to actual time and effort as the attack vector and target audience is larger. The attacks might not be as specific, but the sheer number of victims involved actually make up for the lack of specificity and the number of laymen falling victim of a craftily construed target vehicle is often more in number making this a rather lucrative tool in the hands of a good perpetrator of the said attack
For a couple of days now, I have been the victim of a pretty specific attack and I thought I should write about this, not for the fun of it, but rather, to objectively look at the attack and break it down so we have a good understanding of the attack – as this one, specifically, came across as just a bit more mature than the crude Nigerian Prince that we all have by now, become all too familiar with.
So this is how this plays along. I have a weird habit of once-in-a-while clicking in my mail spam folder and glancing around to see how many spam emails the system was able to auto detect and keep out of my inbox. Usually, I go ahead and do a Delete All and don’t bother with opening any of the emails that are in there. But this time, when I quickly glanced down, this one specific email caught my eye right away
Gmail has a nice way of filtering your emails and in Spam, you usually glance through the usual Senders etc – but Gmail DOES actually show you the message Subject 🙂 So this can be targeted to get your attention! And this email’s subject just said “redhat78” 🙂
So, ofcourse I absolutely HAD to open it! Because you see, redhat78 was one of my email addresses, when the internet was a far more homely place way back in – hold on to your horses – 1999 🙂
And yes, that was a password I used on “disposable” sites – like hallmark etc (yes it was a thing) and other sites I really could not be bothered about much. These were sites like Yahoo or Hotmail or MySpace etc where almost all information provided, including my DOB were purposely incorrect. And these were my “test” mules with regards to subscribing to sites I knew would spam me for the rest of my living years!
So ofcourse I clicked on the email. Gmail had a BIG LARGE RED warning on the mail warning me it was Spam! Which I got rid of, I mean, who the heck really cares
So this was the email in it’s entirety
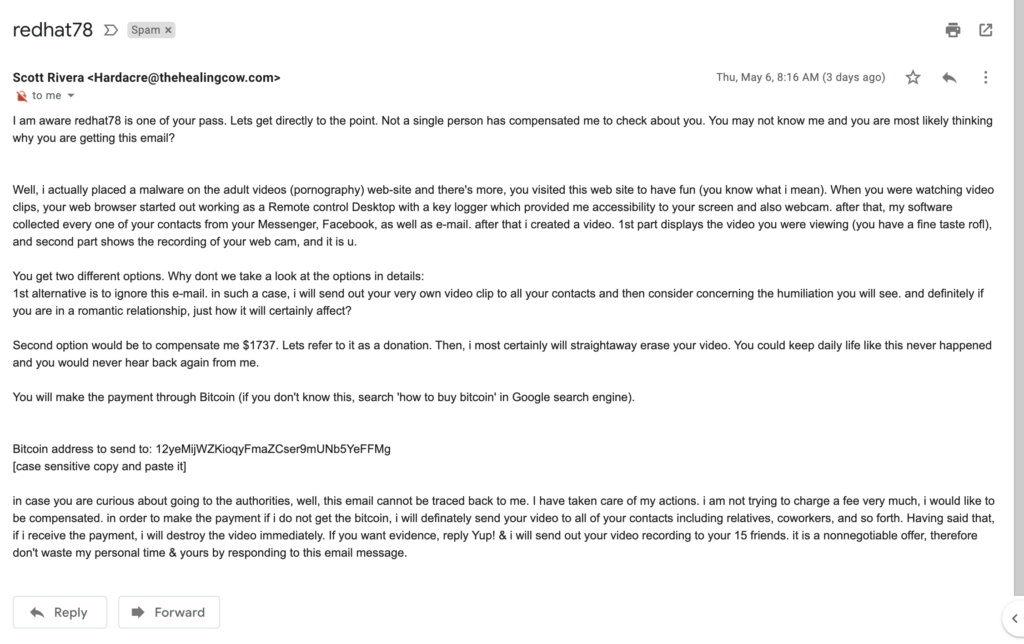
Which is pretty fun and all that, but I was actually struck by how well crafted this mail was! Not that it will win any prizes in creative writing or anything, but just how specific it was with regards to how it got my email/password etc. Enough, actually, to make a person who isn’t very technical or still using old passwords, really sit up and notice and maybe even start researching on Bitcoins!
To me, it’s actually interesting to see how well crafted this is from an attack perspective. So let’s break this down
- This came in to my email address that I know for sure was leaked round about six months ago – how do I know this? Well Google Password checkup and https://haveibeenpwned.com/ told me so! Do I trust https://haveibeenpwned.com/ ? Well no, not really. I also do generic searches and have a script running that will notify me everytime my core details like name, email address, phone number etc are compromised. But generally, I update my core passwords monthly 🙂 And have 2FA on as well – the least I can do
- The password quoted is something I immediately recognised – and which is now freely available across the web and had been for a while now. So that password combination is now no longer used anywhere
- Porn? Really? I mean show me a normal human being who hasn’t probably clicked on something they shouldn’t have atleast once in their lifetimes 🙂 So this shows you the attack vector – which in this case, is EVERYONE reading this blessed email – impressive to say the very least! Extremely well played!
- Keylogger? Here is where things start to not make a lot of sense. Let’s say you DO install a keylogger – God knows there are tons of them around and a drive-by or a drop attack is fairly common. So hold on, you caught me with my pants down (literally) watching and doing you know what whilst at the same time logging my keystrokes? That’s pretty weird for sure! Or do you mean you left the keylogger there for a while? Which then logged in to “Messenger”? What messenger? Facebook? You could have just swiped my contacts from Outlook, no? Why Facebook? And I don’t even have a Messenger or Facebook account? This is where I am afraid things just fall apart and I have lost interest
- The next bits are the contacts and video and yada yada yada – by which point I am already past bored
- And what’s with the $1737 anyways? It almost reads like a credit card outstanding that needs settlement!
So this is how this works out
Step 1 – gather a list of email addresses and compromised passwords – doesn’t matter how far back the passwords go. All that matters is that the recipient can remember the username/email/password combo
Step 2 – create a script/ template for your email
Step 3 – locate an SMTP instance that allows anonymous sending of your email – God knows there are literally tons of them around
Step 4 – in your script, take the password and email combination and start sending out email with the subject and first list of the email containing a specific easy to remember password from the password list. The point is, NEVER use the name of the person anywhere – I mean if I am a script junkie and scripting this, I would not like too much complication, now, would I? And also it just complicates matters a little – what’s in a name anyways?
Step 5 – sit back and watch the moolah come in 🙂
The beauty of this approach is the sheer number of people you can get to – as within the realms of reason, you will hit the bulls eye in almost 2/3 emails sent as almost 2/3 people actually HAVE a Facebook account and/or some kind of a “messenger” app – this one is purposely kept vague as as long as you have Facebook by virtue of implication, Messenger could imply any of the default messaging apps you actually use 🙂
So of course I wrote back asking the sender a bunchload of counter questions, but I am pretty sure am not getting any answers 🙂
I will update this thread as soon as I hear back or become a mini celeb for watching porn in my room whilst logging into FB or Messenger or whatever else the Keylogger had going up it’s sleeve 🙂

